Endpoint security is the practice of securing individual devices—such as computers, mobile phones, tablets, servers, and IoT devices—from cyber threats. Since these endpoints serve as entry points to a network, they are prime targets for hackers, malware, and unauthorized access attempts.
With increasing cyber threats, remote work, and cloud-based applications, organizations must implement strong endpoint security measures to:
- Prevent data breaches and cyberattacks
- Ensure regulatory compliance
- Protect against malware, ransomware, and phishing attacks
- Enhance overall cybersecurity and threat response

we provide Privileged Access Management (PAM) and Data Access Management (DAM) solutions to help businesses secure critical assets, prevent unauthorized access, and meet compliance requirements. Our advanced solutions ensure only authorized users have controlled access to sensitive data and privileged accounts.
✔ Just-in-Time (JIT) Access – Grant privileged access only when required and revoke after use.
✔ Password Vaulting & Rotation – Securely store, encrypt, and rotate privileged credentials.
✔ Session Monitoring & Recording – Track, log, and audit all privileged user activities.
✔ Least Privilege Enforcement – Restrict users to minimum access needed for their role.
✔ Multi-Factor Authentication (MFA) for Privileged Accounts – Prevent unauthorized access.
✔ Compliance Support – Ensure SOX, GDPR, HIPAA, and ISO 27001 compliance.
✔ Access Governance & Control – Define who can access, edit, or share data.
✔ Real-Time Data Monitoring – Track and analyze data access patterns to detect anomalies.
✔ Role-Based & Attribute-Based Access Control (RBAC/ABAC) – Assign data permissions based on user roles or attributes.
✔ Data Encryption & Masking – Protect sensitive data from unauthorized exposure.
✔ Cloud & On-Premise Integration – Secure data across databases, file servers, and cloud platforms.
✔ Audit & Compliance Reporting – Automate reporting for regulatory compliance.
we provide Endpoint Detection & Response (EDR), Extended Detection & Response (XDR), and Secure Access Service Edge (SASE) solutions to help businesses stay ahead of cyber threats. Our solutions offer real-time threat detection, response automation, and secure network access, ensuring comprehensive security across your IT infrastructure.
✔ Behavior-Based Threat Detection – Identify advanced malware, ransomware, and zero-day attacks.
✔ Automated Incident Response – Contain and remediate threats with AI-driven automation.
✔ Forensic Analysis & Threat Hunting – Investigate security incidents and proactively stop breaches.
✔ Centralized Visibility & Reporting – Monitor endpoint activity in real-time.
✔ Seamless Integration with SIEM & SOC – Improve threat intelligence sharing for better security insights.

✔ Cross-Layer Threat Correlation – Detect multi-vector attacks across different security layers.
✔ AI-Driven Threat Analytics – Use machine learning to prioritize security alerts.
✔ Automated Playbooks for Threat Response – Accelerate remediation across the entire IT ecosystem.
✔ Centralized Security Operations Dashboard – Gain 360° visibility of your security posture.
✔ Advanced Threat Intelligence Integration – Leverage global threat intelligence to stay ahead of cyber risks.
✔ Zero Trust Network Access (ZTNA) – Verify every user and device before granting access.
✔ Cloud-Delivered Firewall & SWG – Protect users and applications from cyber threats.
✔ Secure SD-WAN Integration – Optimize performance with encrypted traffic routing.
✔ Data Loss Prevention (DLP) & CASB – Prevent unauthorized data access and leakage.
✔ AI-Driven Network Security – Enhance security with machine learning-driven threat detection.

we offer Multi-Factor Authentication (MFA) solutions to protect businesses, applications, and user accounts from unauthorized access. By requiring multiple authentication factors, MFA enhances security, prevents credential theft, and reduces cyber risks.
✔ One-Time Passwords (OTP) – Secure SMS, email, or authenticator app-based verification.
✔ Biometric Authentication – Use fingerprint, facial recognition, or retina scans for access.
✔ Hardware Tokens & Smart Cards – Physical authentication for high-security environments.

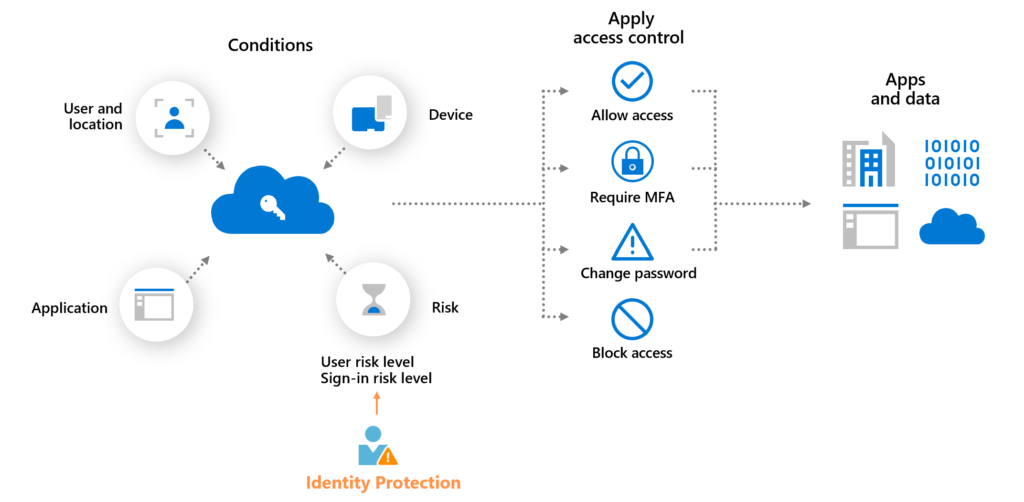
✔ Context-Aware Authentication – Verify users based on location, device, and behavior.
✔ AI-Powered Risk Analysis – Detect suspicious login attempts and prevent breaches.
✔ Customizable Security Policies – Define access rules based on roles and risk levels.
